因為資安威脅的日益演變,組織必須假定電腦與網路系統已經遭到滲透,應該要設法找出隱藏的惡意軟體,而這樣的主動、積極的方法,就稱為威脅獵捕。
網路犯罪通常會潛伏長達191天,security operations center (SOC) 分析團隊通常可以防護到80%的威脅。
先決條件,必須要了解系統與網路架構,以及正常運作時應有的樣子
Priority Intelligence Requirement(優先情報需求)
To set up the questions that will drive your threat hunting efforts and the answers that will drive decision-making within the organization
You should decide which IoCs to look for based on an informed hypothesis. For example, certain changes in traffic flows could indicate data exfiltration.
使用工具集合以及處理流程: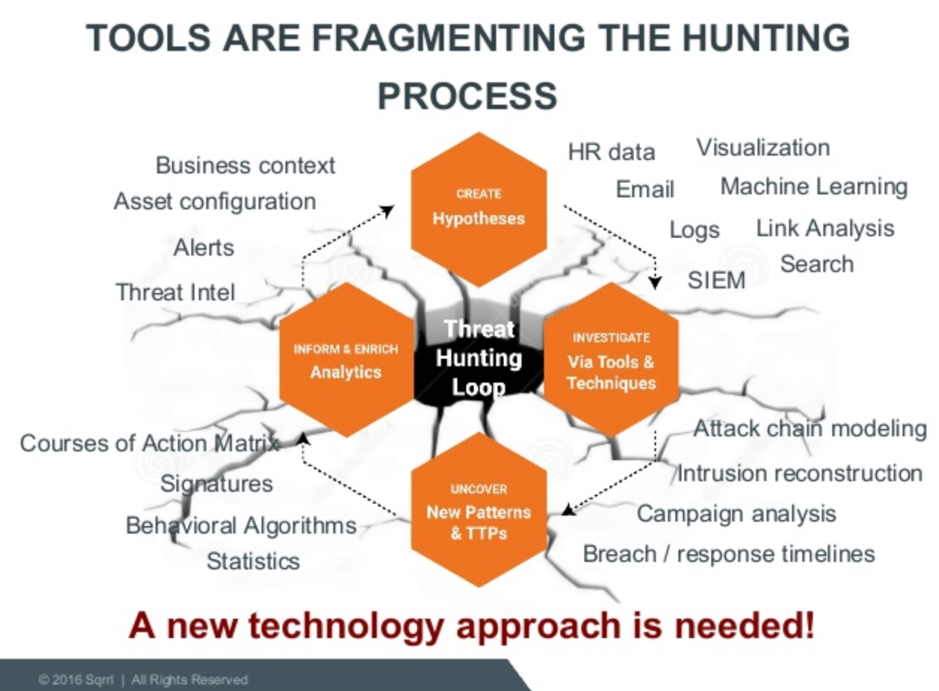
Threat hunting platform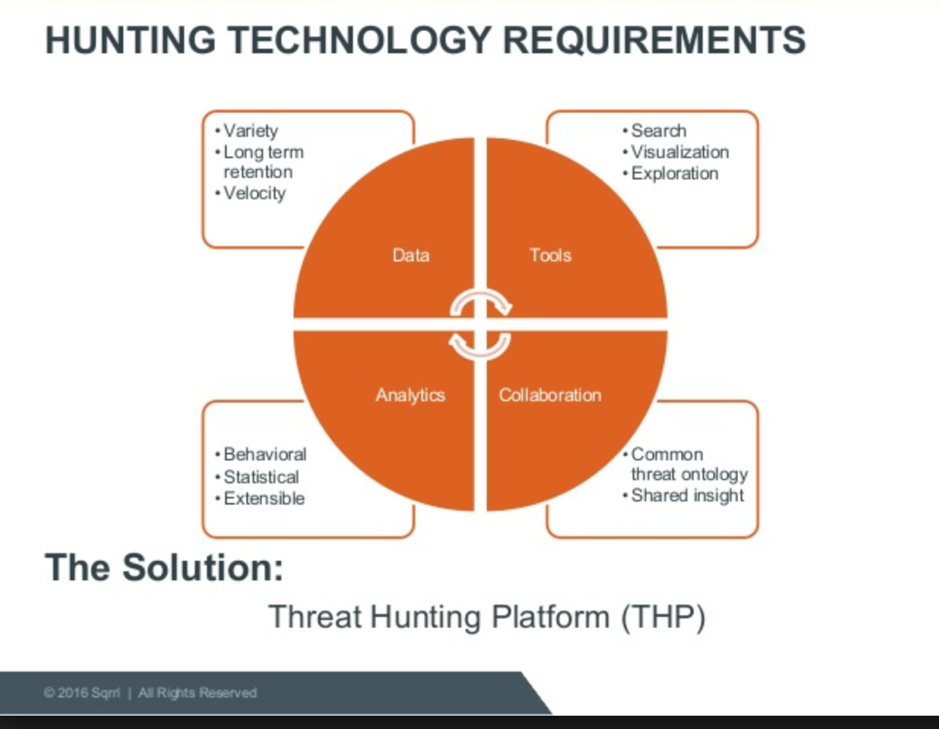
參考來源:
Threat Hunting:面對內部威脅,應採取積極探尋的方式,從被動反應改為主動防禦
https://www.ithome.com.tw/news/122072
A Beginner’s Guide to Threat Hunting
https://securityintelligence.com/a-beginners-guide-to-threat-hunting/
Threat Hunting Platforms (Collaboration with SANS Institute)
https://www.slideshare.net/sqrrl/threat-hunting-platforms-collaboration-with-sans-institute
